
Uncle Ted Uncle Ted Uncle Ted
The Industrial Revolution of digital security and its consequences have been a disaster for personal privacy. It is time to reclaim your digital sovereignty.
Begin TutorialA Cabin in the Digital Woods
Modern technology promises connection but delivers control. Your device is not your own; it is a node in a system designed for surveillance and manipulation. Uncle Ted is not merely an app—it is a declaration of independence. It transforms your device from a liability into a fortress, a digital cabin where you are the sole master. It operates on the principle that true freedom requires absolute control over one's own property and information.
"The degree of personal freedom that exists in a society is determined more by its technological structure than by its laws. We provide the structure for your freedom."
Installation & Initial Setup
Proper configuration is critical for Uncle Ted to function. Follow these steps precisely to arm your device. This process involves granting high-level permissions that enable the app's core security functions.
Step 1: Installation
Uncle Ted is too powerful for the Google Play Store. You must install it manually.
- Download the latest
app-release.apkfile from the project's official GitHub repository. - Open the downloaded APK file on your Android device.
- You will likely need to grant your browser or file manager permission to "Install unknown apps". This is a standard security measure.
- Follow the on-screen prompts to complete the installation.
Step 2: Granting Core Service Permissions
Upon opening Uncle Ted for the first time, you will be greeted by the Core Services screen (PermissionsFragment). This screen is your checklist for activating the app's foundational protections. You must enable all services for the app to function correctly. Each button will take you to the relevant system settings page.
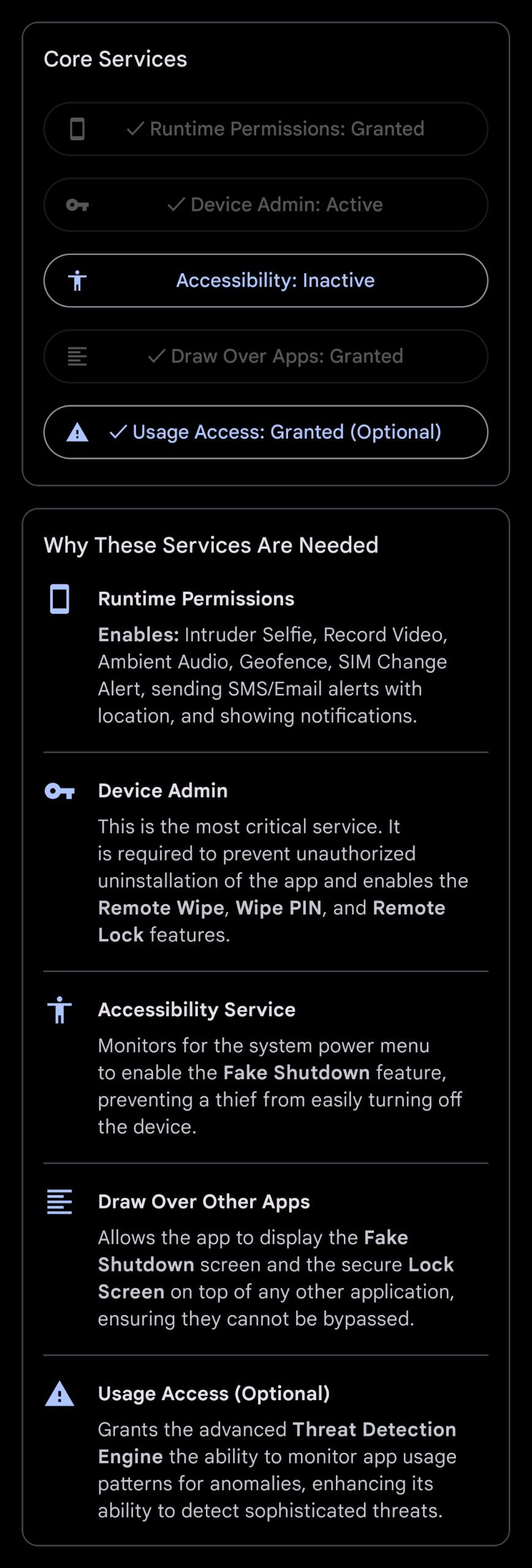
The Core Services screen is the first step to securing your device.
- Runtime Permissions: This is the first and most basic step. It grants access to the camera, microphone, location, SMS, notifications, and more. These are essential for evidence collection and sending alerts.
- Device Admin: This is the most critical permission. It gives Uncle Ted the power to remotely lock the device, wipe all data, and prevent unauthorized uninstallation. Without this, the app's anti-theft capabilities are severely limited. When you attempt to disable this service later, the
AdminReceiverwill intercept the action and lock the device unless Maintenance Mode is active. - Accessibility Service: This service (
PowerButtonService) monitors the system for when the power menu is opened. This is required for the Fake Shutdown feature, allowing the app to display a fake screen while remaining operational. - Draw Over Other Apps: This permission allows Uncle Ted to display its secure
LockScreenActivityandFakeShutdownActivityon top of any other application, including the system UI. This ensures its security screens cannot be bypassed. - Usage Access (Optional): This grants the advanced
ThreatDetectionEnginethe ability to monitor app usage patterns for anomalies, enhancing its ability to detect sophisticated threats. While optional, it is highly recommended for maximum security.
The Dashboard: Your Security Command Center
The Dashboard is the main screen of the application (DashboardFragment). It provides an at-a-glance overview of your device's security posture, potential threats, and configuration status.
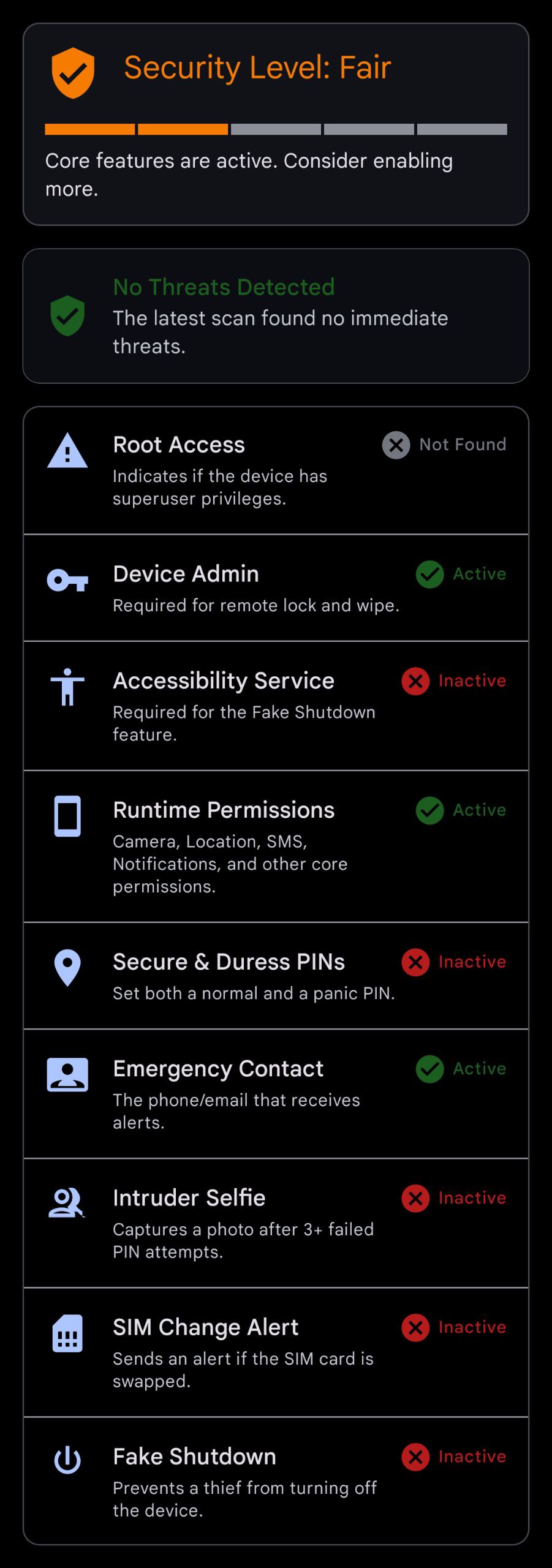
The Dashboard shows your security level, active threats, and configuration checklist.
Security Level Meter
At the top of the screen, a 5-stage progress bar and status title indicate your current security level. This score is calculated by the SecurityScoreCalculator based on which critical features and permissions you have enabled. The levels are:
- Level 0 (Compromised): Device Admin is not active. The app is effectively useless.
- Level 1-2 (Poor/Fair): Basic permissions are granted, but key features are disabled.
- Level 3-4 (Good/Excellent): Most protective features are active.
- Level 5 (Maximum): All standard security features are enabled and configured.
- Level 6 (God Mode): Root access is detected. You have unlocked ultimate control.
Threat Assessment
This card, powered by the ThreatDetectionEngine and AISecurityOrchestrator, dynamically analyzes your device for suspicious activity. It flags potential threats such as rapid app installations, unexpected VPN usage, or anomalous data consumption, assigning a threat level from Minimal to Critical.
Security Checklist
This is a detailed list of the individual components contributing to your security score. Each item shows its status (Active/Inactive) and provides a brief description of its purpose. Use this checklist to identify and enable any remaining security features.
Core Features Arsenal
These are the primary tools at your disposal, configurable via the Authentication, Remote Control, and Features tabs in the app. They form a layered defense against theft and unauthorized access.
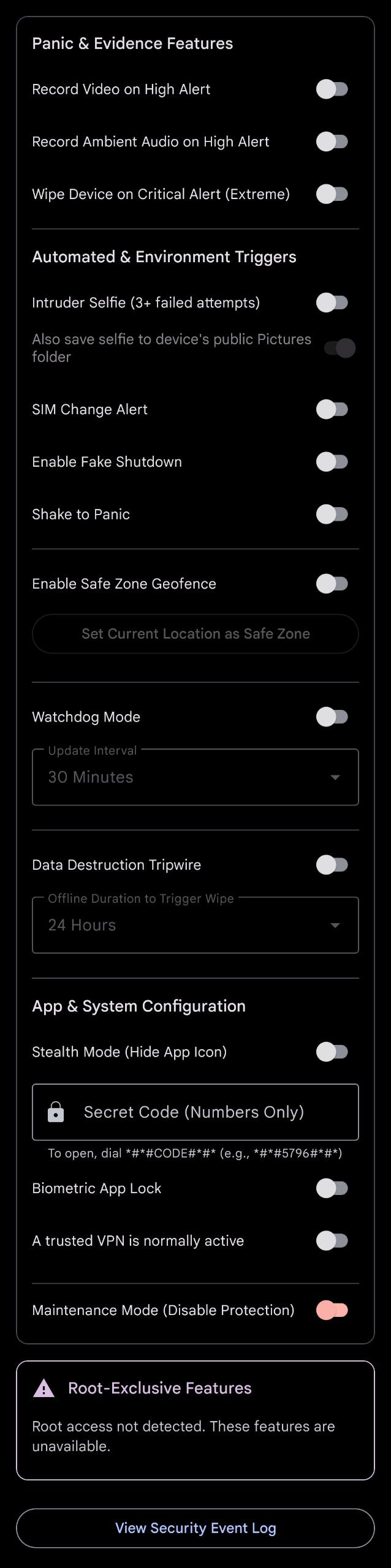
The Features screen allows you to enable and disable various security triggers.
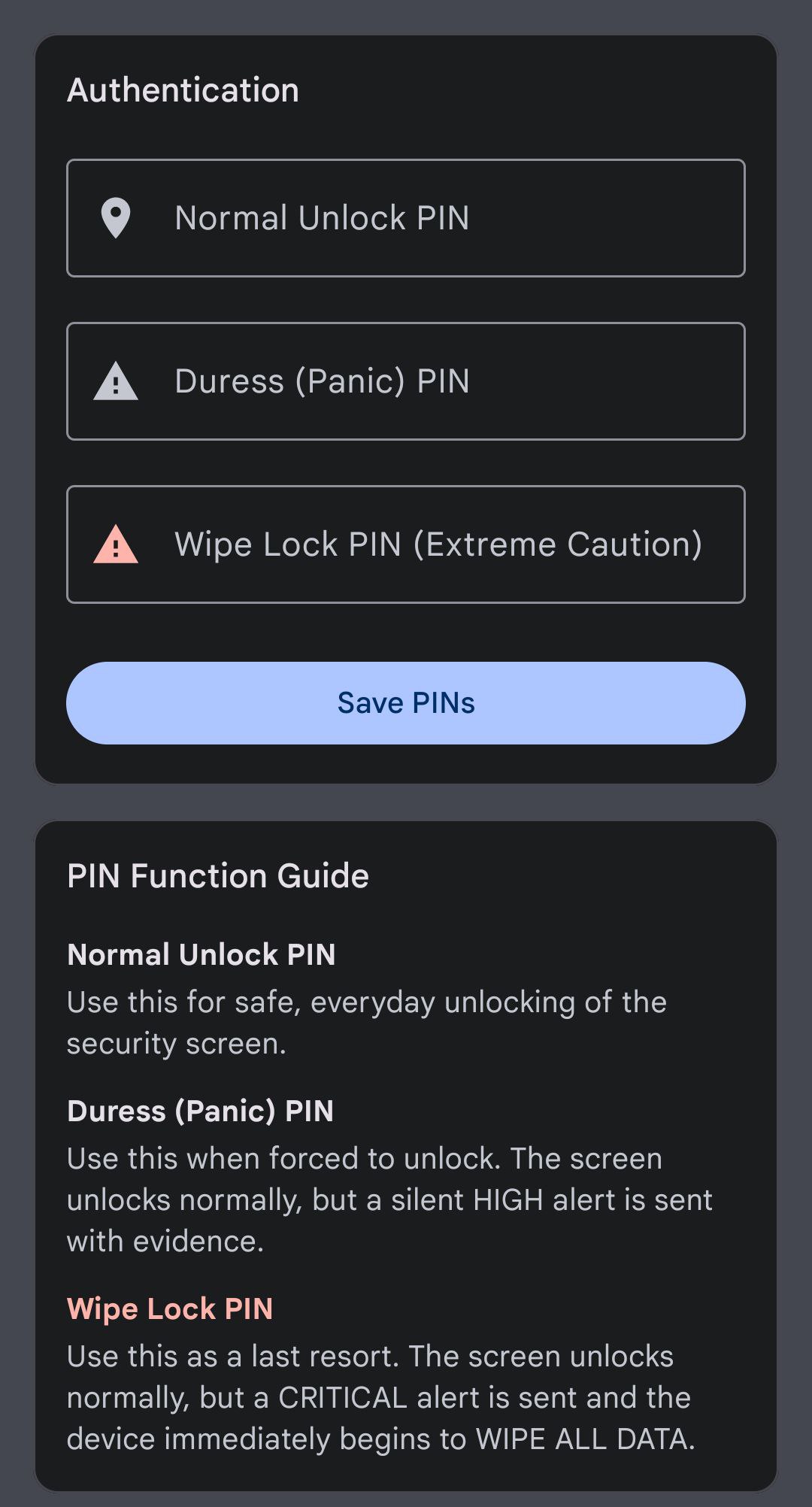
Multi-Level Authentication
Configure three distinct PINs in the Authentication tab (PinsFragment) for different scenarios. The LockScreenActivity will react based on the PIN entered.
Normal PIN: Safely unlocks the device.Duress PIN: Unlocks the device but silently triggers a HIGH severity alert.Wipe PIN: Unlocks the device but triggers a CRITICAL severity alert and initiates a full device wipe.
Intruder Selfie
When enabled, the app logs failed unlock attempts. After 3 or more failures, it triggers a MEDIUM severity alert, activating the PanicActionService to discreetly take a photo using the front camera.
Fake Shutdown
Requires the Accessibility Service. When a user tries to open the power menu, Uncle Ted intercepts it and displays a convincing fake shutdown screen (FakeShutdownActivity). The device appears off but remains fully active, sending alerts and evidence.
SIM Change Alert
The SimChangeReceiver constantly monitors the device's SIM card serial number. If it is changed or removed, a MEDIUM alert is triggered, notifying you of potential theft.
Shake to Panic
When enabled, the MonitoringService uses the accelerometer to detect vigorous shaking. This triggers a HIGH severity panic alert, useful for situations where you cannot interact with the screen.
Stealth Mode
Hides the application's icon from the launcher by disabling its activity-alias. The app can then only be opened by dialing a secret code (e.g., *#*#1234#*#*) which is detected by the SecretCodeReceiver.
Watchdog Mode
A periodic "proof-of-life" service. The WatchdogWorker runs at a configured interval (e.g., every 30 minutes) and sends a status update with battery and location information to your emergency contact. This confirms the device is still operational.
Data Destruction Tripwire
An extreme security measure. If the device fails to connect to the internet for a pre-defined duration (e.g., 24 hours), the TripwireWorker assumes the device is captured and offline. It will trigger a CRITICAL alert and initiate a full device wipe.
Safe Zone Geofence
Set a geographical "safe zone" (e.g., your home). If the device leaves this area, the GeofenceBroadcastReceiver will trigger a LOW severity alert, notifying you that the device is on the move.
God Mode: Root-Exclusive Dominance
For those who refuse to compromise. Root access unlocks Uncle Ted's most potent, system-level capabilities, managed in the Features tab. These actions, executed by RootActions.kt, operate below the standard Android framework, offering unparalleled persistence and control. Warning: Use of these features is for advanced users and assumes all legal and ethical responsibility. Misuse can permanently damage your device.
Survive Factory Reset
EXTREME DANGER: Attempts to flash a loader script to the recovery partition. This loader can re-install Uncle Ted after a factory reset. A wrong script or URL WILL BRICK YOUR DEVICE.
System App Conversion
Moves the application into the /system/priv-app directory, making it a core part of the OS and immune to standard uninstallation methods. This requires a reboot and is irreversible without root.
Unkillable Service
Deploys a root-level init.d script. This script runs at boot and constantly monitors and restarts the app's core services if they are ever terminated, ensuring true persistence.
Kernel-Level Keylogger
Directly reads input events from the kernel using getevent, capturing all keystrokes before they reach the OS. Logs can be remotely exfiltrated via SMS command.
Stealth Media & Screenshots
Utilizes the command-line screencap utility to capture the screen silently. Can also attempt to kill the cameraserver process to suppress the camera/mic privacy indicators (the "green dot").
App Data Exfiltration
Breaches the Android security sandbox to directly copy files from other apps' private data directories (e.g., /data/data/com.whatsapp/databases/msgstore.db).
Remote Command & Control
Uncle Ted can be fully controlled via SMS commands, processed by the SmsCommandReceiver. Configure your emergency contact and a master password in the Remote Control tab.
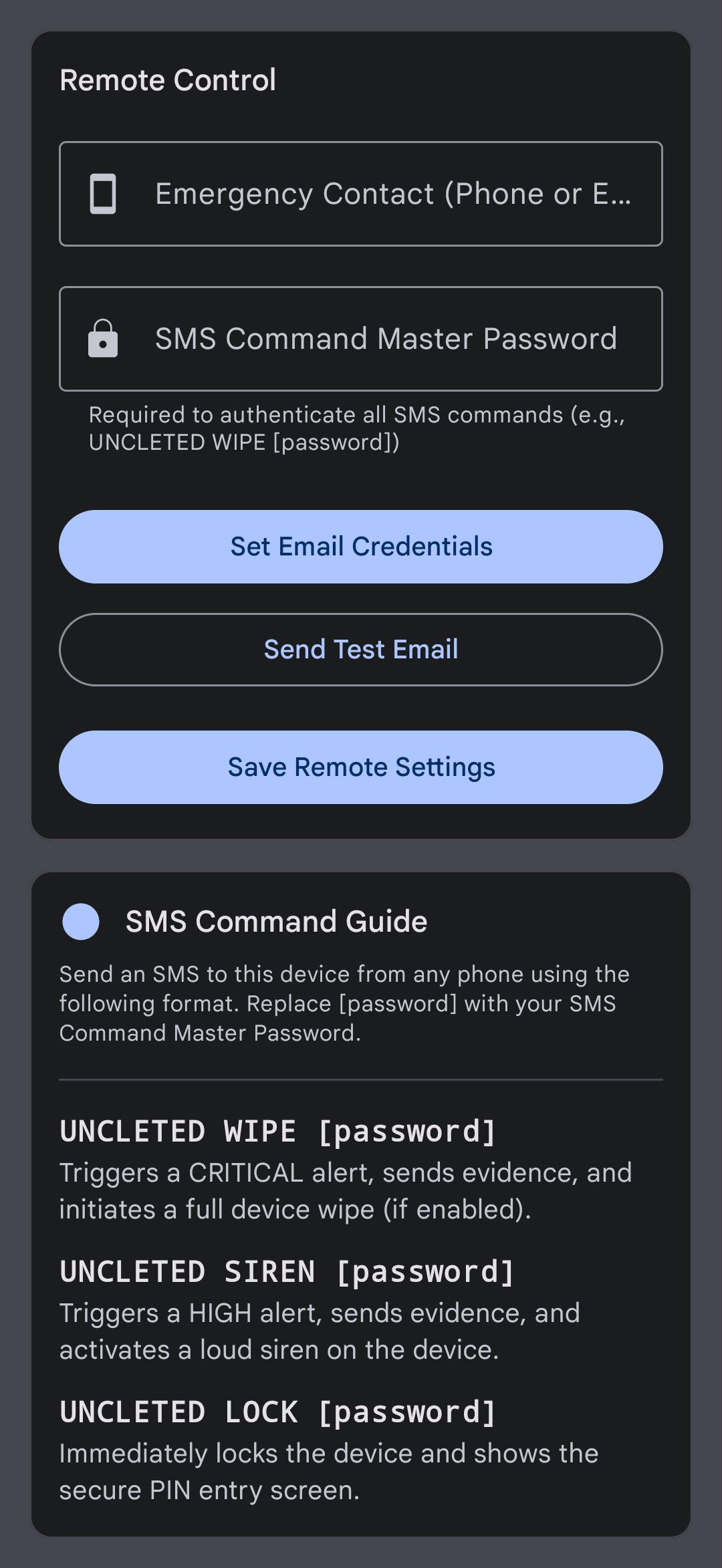
Configure your emergency contact and master password for SMS commands.
Setup
- Emergency Contact: Enter a phone number or email address. Alerts will be sent here. If a phone number is used, only basic text alerts can be sent. For full evidence packages (photos, videos, audio), an email address is required.
- SMS Command Master Password: Set a strong, unique password. This password is required to authenticate every remote command, preventing unauthorized control of your device.
- Email Credentials: For email alerts, you must provide the SMTP server details for a sender email account. It is highly recommended to use an "App Password" for services like Gmail, not your main account password.
SMS Command Syntax
Send an SMS to the device with the following format. Commands are not case-sensitive. Replace [password] with your actual master password.
UNCLETED [COMMAND] [ARGUMENTS] [password]Available Commands
-
LOCK: Immediately locks the device screen.
UNCLETED LOCK mySecretPass123 -
SIREN: Triggers a HIGH severity alert and plays a loud siren.
UNCLETED SIREN mySecretPass123 -
WIPE: Triggers a CRITICAL alert and initiates a full device data wipe.
UNCLETED WIPE mySecretPass123 -
SCREENSHOT (Root): Takes a stealth screenshot and emails it to the emergency contact.
UNCLETED SCREENSHOT mySecretPass123 -
GETLOGS (Root): Emails any captured keylogger data to the emergency contact and clears the log.
UNCLETED GETLOGS mySecretPass123 -
EXFIL (Root): Exfiltrates a specific file from another app's data folder and emails it as an attachment.
UNCLETED EXFIL com.whatsapp databases/msgstore.db mySecretPass123
Legal & Ethical Disclaimer
This application is designed for educational and defensive security purposes ONLY. Features like stealth operations, remote data access, and data destruction carry significant ethical and legal responsibilities. Never install or use this application on a device without the owner's explicit and informed consent. Unauthorized use is strictly prohibited and may lead to severe legal consequences. The developer assumes no liability for any misuse of this software.